What is SecureScan?
SecureScan is an innovative application that uses advanced AI to analyze emails for phishing threats and leverages blockchain technology to maintain the integrity and traceability of email analysis. This dual approach ensures that users are not only alerted to potential phishing attempts but can also verify the authenticity of the analysis, thanks to the immutable nature of blockchain.
Key Features of SecureScan
Advanced AI Email Analysis:
Utilizes the latest models from OpenAI to evaluate the content of emails.
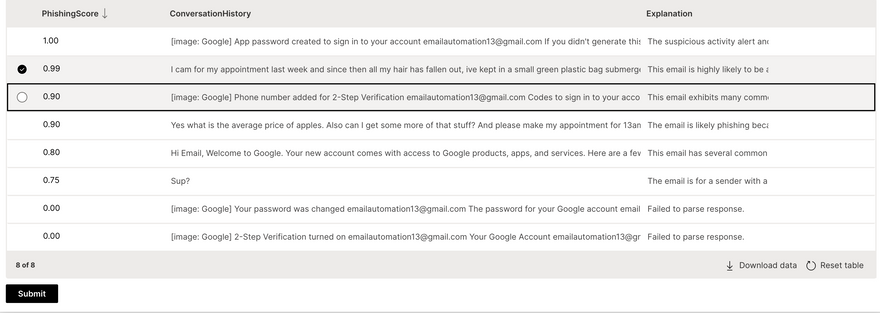
Scores emails based on their likelihood of being a phishing attempt, providing users with a clear metric of threat level.
Offers detailed explanations for each score, helping users understand why an email was flagged as suspicious.Blockchain-Enhanced Security:
Stores hashes of analyzed emails on the XinFin Network, an Ethereum-compatible blockchain platform, ensuring data integrity.
Allows users to verify the authenticity of the email analysis at any time, providing a reliable method to contest or confirm phishing allegations.
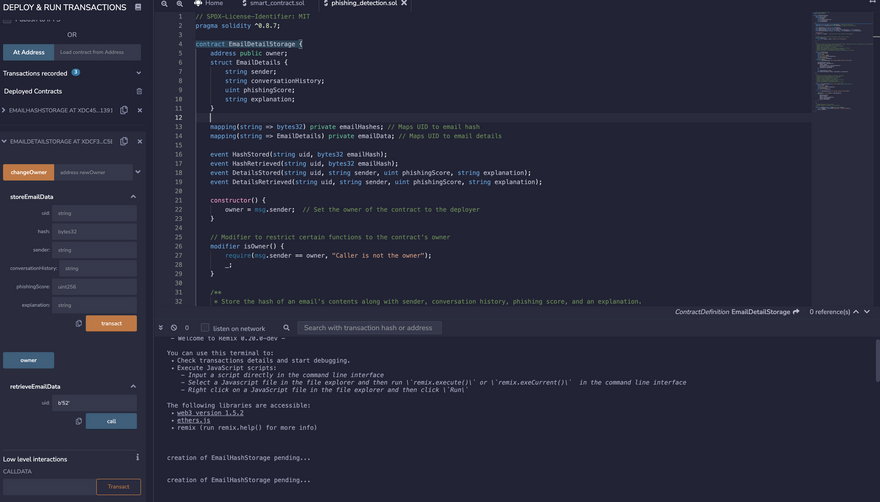
Deployed smart contract
User-Friendly Interface:
Built with H2O Wave, the app features a sophisticated yet intuitive user interface that makes navigation and operation as straightforward as possible.
Real-time updates and interactive elements ensure a responsive user experience, tailored for both technical and non-technical users.
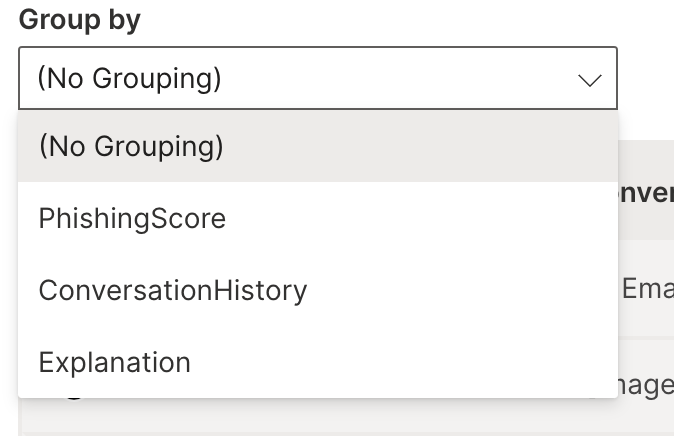
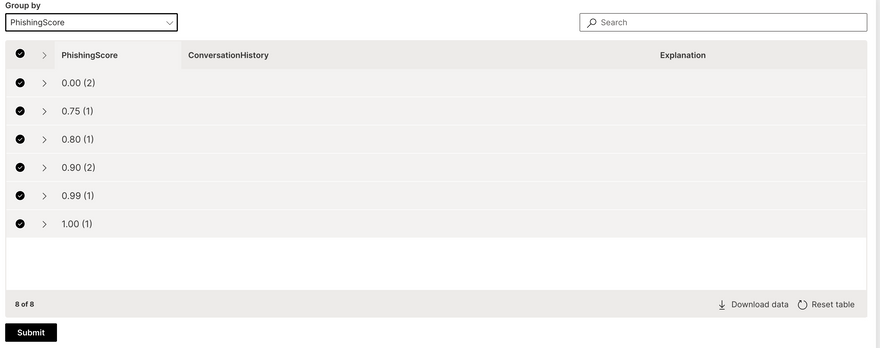
Grouping Searching Filtering can be used to get required emails with ease
Comprehensive Email Fetching:
Integrates securely with email servers using IMAP over SSL, protecting users as they fetch and analyze emails.
Compatible with all major email providers, ensuring that it can be widely used without compatibility issues.
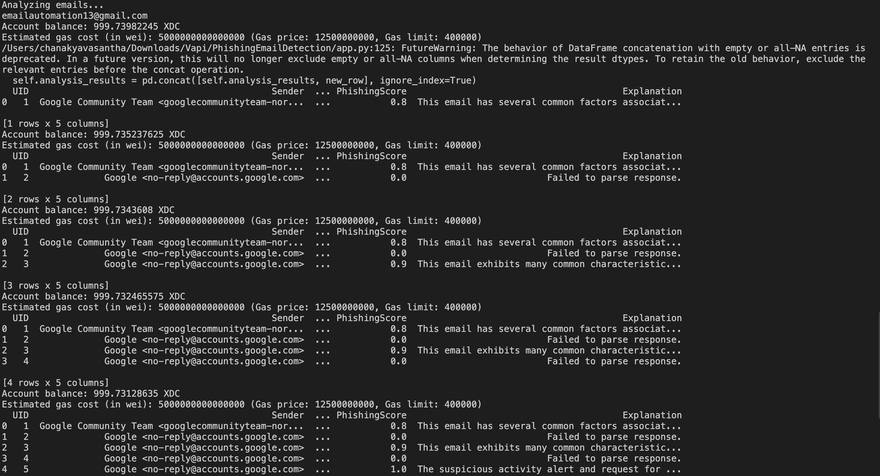
Emails fetched are getting Stored on XDC Block Chain.
How SecureScan Works?
Login and Fetch: Users log in with their email credentials. SecureScan fetches emails directly from their inboxes using encrypted connections.
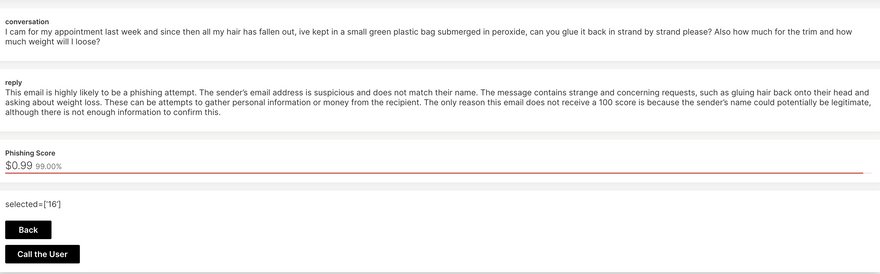
Analyze: Each email is analyzed by AI based on its content and metadata. The AI model scores each email and provides a detailed explanation of its findings.
Here We have the advantage of prompting according to a organization needs to detect phishing emailsStore and Verify: For each analyzed email, a hash is generated and stored on the blockchain. This hash serves as proof of the email's content at the time of analysis.
Special Feature of SecureScan:
Automated AI Voice Calling Assistant for Phishing Awareness: SecureScan includes an innovative feature where an automated AI voice assistant proactively calls users to inform them about potential organization-specific phishing threats. Administrators can utilize this assistant to alert users about possible spam and malicious attacks that are tailored to their organization's unique security concerns. This proactive communication helps in educating and preparing users against specific tactics that cyber attackers might use against them.
select an email to see the detailed phishing analysis report
you can click on the call user button to call the user, to let them know about the phishing email and how to react to it. The AI Assistant converses in realtime with the user
Smart Contract To store Email Data:
// SPDX-License-Identifier: MIT
pragma solidity ^0.8.7;
contract EmailDetailStorage {
address public owner;
struct EmailDetails {
string sender;
string conversationHistory;
uint phishingScore;
string explanation;
}
mapping(string => bytes32) private emailHashes; // Maps UID to email hash
mapping(string => EmailDetails) private emailData; // Maps UID to email details
event HashStored(string uid, bytes32 emailHash);
event HashRetrieved(string uid, bytes32 emailHash);
event DetailsStored(string uid, string sender, uint phishingScore, string explanation);
event DetailsRetrieved(string uid, string sender, uint phishingScore, string explanation);
constructor() {
owner = msg.sender; // Set the owner of the contract to the deployer
}
// Modifier to restrict certain functions to the contract's owner
modifier isOwner() {
require(msg.sender == owner, "Caller is not the owner");
_;
}
/**
* Store the hash of an email's contents along with sender, conversation history, phishing score, and an explanation.
* @param uid the unique identifier for the email
* @param hash the SHA-256 hash of the email's contents
* @param sender the sender of the email
* @param conversationHistory the conversation history as a string
* @param phishingScore the phishing score as an integer
* @param explanation the explanation regarding the phishing score or email
*/
function storeEmailData(
string calldata uid,
bytes32 hash,
string calldata sender,
string calldata conversationHistory,
uint phishingScore,
string calldata explanation
) external isOwner {
require(emailHashes[uid] == 0, "Data already exists for this UID");
emailHashes[uid] = hash;
emailData[uid] = EmailDetails({
sender: sender,
conversationHistory: conversationHistory,
phishingScore: phishingScore,
explanation: explanation
});
emit HashStored(uid, hash);
emit DetailsStored(uid, sender, phishingScore, explanation);
}
/**
* Retrieve the hash and details of an email using UID.
* @param uid the unique identifier for the email
* @return hash the SHA-256 hash of the email
* @return sender the sender of the email
* @return conversationHistory the conversation history
* @return phishingScore the phishing score
* @return explanation the explanation about the email
*/
function retrieveEmailData(string calldata uid) external view returns (
bytes32 hash,
string memory sender,
string memory conversationHistory,
uint phishingScore,
string memory explanation
) {
require(emailHashes[uid] != 0, "No data stored for this UID");
EmailDetails storage details = emailData[uid];
return (
emailHashes[uid],
details.sender,
details.conversationHistory,
details.phishingScore,
details.explanation
);
}
/**
* Change the owner of the contract.
* @param newOwner the address of the new owner
*/
function changeOwner(address newOwner) external isOwner {
require(newOwner != address(0), "New owner is the zero address");
owner = newOwner;
}
}
Helper Function to store data on chain
def store_email_data_on_chain(uid, email_body, sender, conversation_history, phishing_score, explanation):
try:
uid = str(uid) # Ensure UID is a string as expected by the ABI
private_key = '1913b305c73fdd97e6565d6a2c8a0baf51030d52c29a4f847b94b79a1eca32dc'
account = w3.eth.account.from_key(private_key)
email_hash = w3.keccak(text=email_body)
sender_address = account.address
#print(f"Sender Address: {sender_address}")
#print(uid, email_hash, sender, conversation_history, phishing_score, explanation)
# Retrieve account balance
balance = w3.eth.get_balance(sender_address)
print(f"Account balance: {w3.from_wei(balance, 'ether')} XDC")
# Gas estimation
gas_price = w3.eth.gas_price
gas_limit = 400000 # Adjusted for possibly greater transaction complexity
total_cost = gas_price * gas_limit
print(f"Estimated gas cost (in wei): {total_cost} (Gas price: {gas_price}, Gas limit: {gas_limit})")
if balance < total_cost:
return f"Error: Insufficient funds for the transaction. Required: {w3.from_wei(total_cost, 'ether')} XDC, Available: {w3.from_wei(balance, 'ether')} XDC"
# Transaction count (nonce) for the sender's address
nonce = w3.eth.get_transaction_count(sender_address)
# Build the transaction
tx = contract.functions.storeEmailData(uid, email_hash, sender, conversation_history, phishing_score, explanation).build_transaction({
'chainId': 51, # Chain ID for XinFin MainNet, use 51 for Apothem Testnet if necessary
'gas': gas_limit,
'gasPrice': gas_price,
'nonce': nonce,
})
# Sign the transaction with the sender's private key
signed_tx = account.sign_transaction(tx)
# Send the transaction
tx_receipt = w3.eth.send_raw_transaction(signed_tx.rawTransaction)
return tx_receipt.hex()
except Exception as e:
return f"Error: {str(e)}"
helper function to retrieve email data from the chain
def get_email_details(uid):
return contract.functions.getEmailDetails(uid).call()
- github-link: https://github.com/chanakyavasantha/DIMO_HACKS
- Youtube-link: https://youtu.be/1XbpAiQtP_s?si=0AqIfr3MhnVb8Mjl






Discussion (0)